JMP Live Installation Help
JMP Live components must be installed in this order:
Learn how to manage your JMP Live installation:
Install JMP Pro 18
Note: Before you can install JMP Live, you must install JMP Pro 18.
To install JMP Pro 18, double-click the jmppro_1800_win.exe file and follow the on-screen instructions. This file is located in the ZIP file that you downloaded from JMP.
Install the JMP Live Database
The JMP Live Database installation adds the PostgreSQL 14.5 database and a dedicated database for JMP Live, which includes an owner login account and a database schema.
Note: Before proceeding, ensure that the Windows port permissions allow access for any listening ports that you intend to use for JMP Live databases.
Important notes before proceeding
|
•
|
You must be logged in as a Windows Server Administrator user to install the JMP Live database.
|
|
•
|
If this is your first time installing JMP Live, follow the normal installation procedures at Install the JMP Live Database.
|
|
•
|
If you have already installed JMP Live, follow the procedures at Upgrade the PostgreSQL Database.
|
|
•
|
If you have a PostgreSQL database version 14 or higher already installed, you can use SQL instead of the JMP Live Database installer. See Install JMP Live Using an Existing Database.
|
Install the JMP Live Database
|
1.
|
Double-click JMPLiveDatabase.msi.
|
This file is located in the ZIP file that you downloaded from JMP.
Figure 1.1 JMP Live Database Setup Wizard
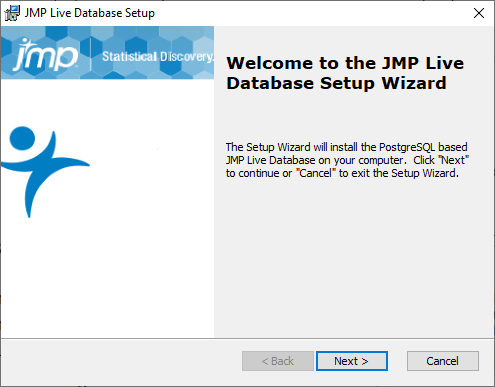
|
2.
|
Click Next.
|
Figure 1.2 Specify Installation Folders
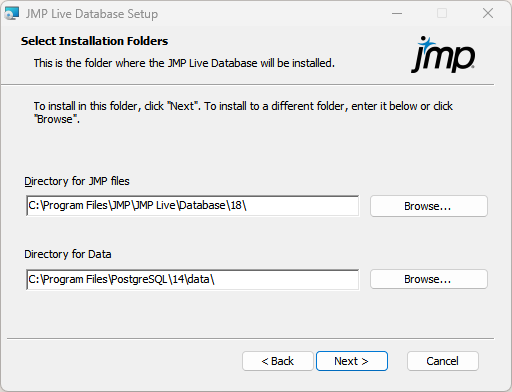
|
3.
|
Specify where to install the JMP Live database and the PostgreSQL database:
|
|
–
|
Click Next to accept the default location.
|
|
–
|
Click Browse to change the default installation folder.
|
Note: Make sure you have adequate space in the directory where you install the PostgreSQL database.
Figure 1.3 Specify Database Parameters
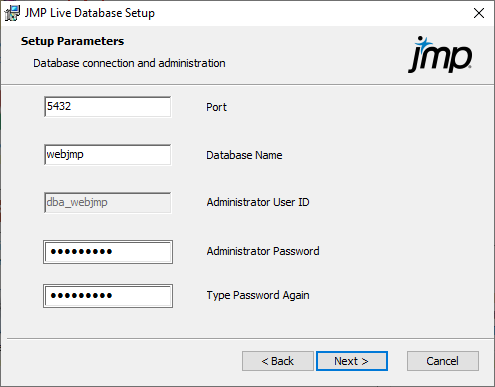
|
4.
|
Enter these parameters:
|
Note: If you are upgrading, ensure that these parameters match what is in your JMP Live environment file. For details, see (Optional) Configure Advanced Settings.
|
–
|
Port: The TCP port that PostgreSQL uses to communicate with other databases. This is usually 5432. If you are upgrading from PostgreSQL 11, this port must be different from the previous database port number. In this case, 5433 is recommended.
|
|
–
|
Database Name: The name of the default database that JMP Live uses. It is recommended to keep this set to webjmp. The administrator user ID cannot be changed from dba_webjmp.
|
|
–
|
Administrator Password: The administrator password, which is Password1 by default. It is strongly recommended that you change this password.
|
Note: Allowable characters are A-Z, a-z, 0-9, and ;,/?:@&=+$#-_.!~*'().
Figure 1.4 Start JMP Live Database Installation
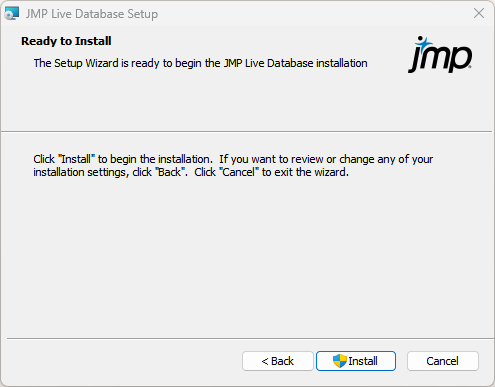
|
5.
|
Click Install.
|
|
6.
|
Click Finish once the installer is done.
|
|
7.
|
Reboot your machine before installing JMP Live, to ensure that the PostgreSQL server starts. You can use the pgAdmin tool to verify that your database has started.
|
Network Security Consideration
During the JMP Live installation, a network permissions file named pg_hba.conf is added to your data drive, located here (by default): C:\Program Files\PostgreSQL\14\data. This file is in a format required by PostgreSQL. The version that JMP provides allows network access to the database from outside of the installed machine. This permits the distribution of the database outside of the machine where JMP Live is installed. If you do not want this type of access, it is important to change the settings in pg_hba.conf accordingly. The file itself contains instructions on how to do this, but you can also search the PostgreSQL site for information.
Upgrade the PostgreSQL Database
When you install or update JMP Live, it is recommended to install the newest version of PostgreSQL that is supplied by JMP. To upgrade the PostgreSQL database, follow the instructions on migrating the database at the PostgreSQL website. In general, this procedure involves these steps:
|
1.
|
Use the pgdump utility with the export large objects option supplied by Postgres to save out a copy of the database.
|
|
2.
|
Uninstall the old version of PostgreSQL, making sure to retain the data directory. This is done by default.
|
|
3.
|
Install the new version of PostgreSQL. Use the same data location as the previous version.
|
|
4.
|
If you do not see your data, use the pgrestore utility supplied by Postgres to load the old data into the new database.
|
Install JMP Live Using an Existing Database
If you already have an existing, compatible version of PostgreSQL installed (14 or higher), instead of installing the JMP Live Database, you can add the required database, schema and log on credentials yourself. Using the pgAdmin tool or other database exploration tools that allow queries, use the following SQL:
CREATE USER dba_webjmp WITH CREATEDB CREATEROLE LOGIN ENCRYPTED PASSWORD 'Password1';
CREATE DATABASE webjmp WITH OWNER dba_webjmp;
\connect webjmp
CREATE SCHEMA IF NOT EXISTS webjmp AUTHORIZATION dba_webjmp;
If you change the default names, you must also change the names in the environment files for JMP Live and JMPPool, where the database access is described. See (Optional) Configure Advanced Settings.
Install Keycloak
Note: Make sure that you install the JMP Live Database before installing Keycloak, and install JMP Live after installing Keycloak.
JMP Live uses Keycloak to manage authentication, such as identity management and access. Behind the scenes, when JMP Live users log on, they authenticate to Keycloak. Keycloak provides federated single sign-on capabilities to many different identity providers, giving JMP Live users familiar access to the product.
Tip: Installing Keycloak is straightforward. Most of the customization to connect to identity providers is done through Keycloak after it is installed and running.
Update Keycloak
If you are upgrading from JMP Live 17 to 18, you must perform these steps:
|
1.
|
Make sure that you have the administrator and database settings for the JMP Live 17 version of Keycloak. You need to use these same details for the JMP Live 18 version of Keycloak.
|
|
2.
|
Uninstall the JMP Live 17 version of Keycloak.
|
|
3.
|
(Optional, recommended) Rename the old Keycloak directory (for example, Keycloak.old).
|
By default, this directory is here: C:\Program Files\SAS\Keycloak.
|
4.
|
Proceed to install the JMP Live 18 version of Keycloak.
|
Install Keycloak
|
1.
|
Double-click Keycloak.exe.
|
This file is located in the ZIP file that you downloaded from JMP.
Figure 1.5 Select Your Setup Language
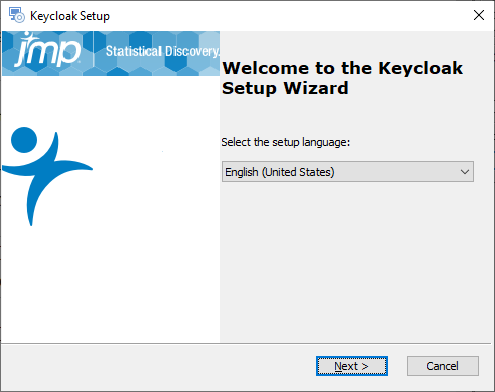
|
2.
|
Select your setup language, and then click Next.
|
Figure 1.6 Keycloak Welcome Window
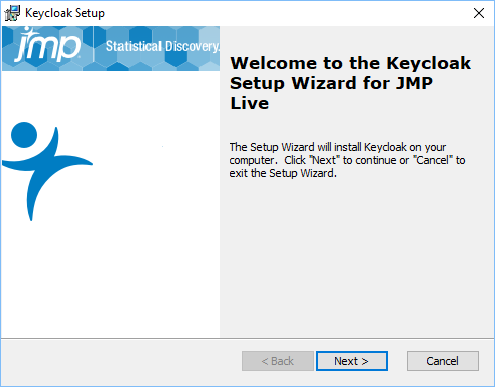
|
3.
|
Click Next.
|
Figure 1.7 Specify the Keycloak Install Location
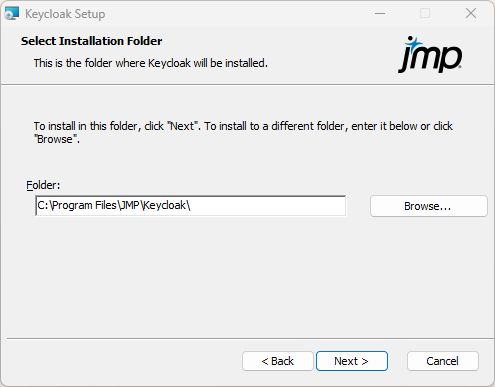
|
4.
|
Specify where you want to put the Keycloak installation files, and then click Next.
|
Note: The Keycloak files are placed in a subfolder in the install directory. This subfolder cannot be moved or changed.
Figure 1.8 Set Up the Keycloak Administrator
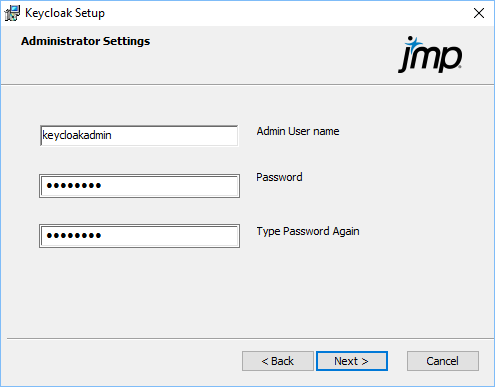
|
5.
|
Specify the administrator credentials, and then click Next.
|
By default, the user name is keycloakadmin and the password is password. It is recommended to change the password.
Figure 1.9 Specify the Java Install Location
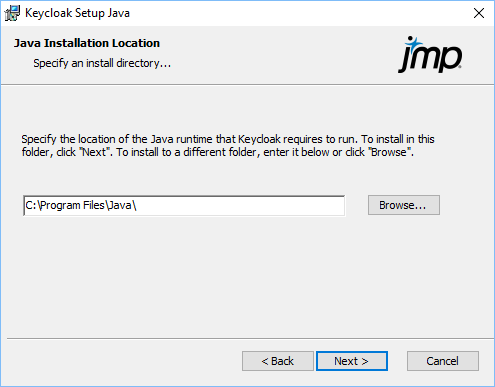
During the Keycloak installation, the Azul Java distribution is also installed. If you already have this installed, no changes are made to your current installation.
|
6.
|
Specify the directory where you want to install Java, and then click Next.
|
Note: The installer adds a JAVA_HOME environment variable to the Windows advanced system settings.
Figure 1.10 Configure Ports and Services
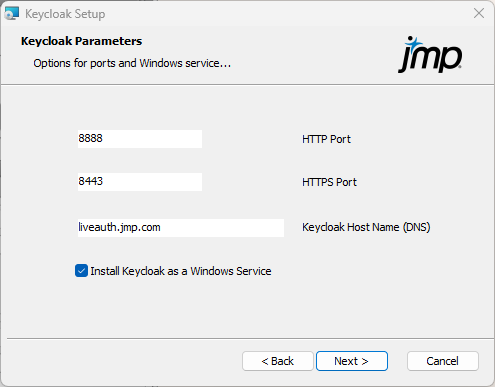
|
7.
|
Specify these Keycloak details:
|
|
–
|
HTTP port: Enter the HTTP network port. The default port is 8888. This port needs to be open to the Keycloak server.
|
|
–
|
HTTPS Port: Enter the HTTPS network port. The default port is 8443. This port needs to be open to the Keycloak server.
|
|
–
|
Keycloak Host Name (DNS): Enter the host name of the Keycloak server.
|
|
–
|
Install Keycloak as a Windows Service: Select this option to install Keycloak as a Windows service. This means that Keycloak is automatically started, and if the machine reboots it automatically restarts, so that Keycloak is always running. If you do not select this option, you must start Keycloak manually the first time and anytime the machine is rebooted. This option is selected by default, and it is recommended to keep it selected.
|
|
8.
|
Click Next.
|
Figure 1.11 Specify Keycloak Certificates
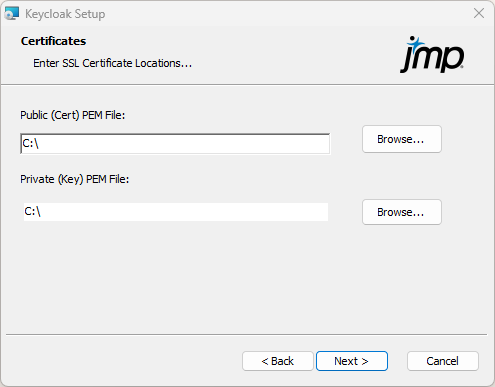
Keycloak requires SSL certificates to guarantee your organization's authenticity and to allow secure connections between Keycloak and identity providers.
Caution: Installation fails if you do not specify these certificates.
|
9.
|
Specify the locations of your organization’s SSL certificates. These must be obtained from an authorized provider.
|
|
–
|
SSL certificates are text files containing cryptographic keys that enable a browser and the web server to have secure communication. These keys are specific to an organization and are provided by third-party vendors like DigiCert, Symantec, and Network Solutions. JMP Live cannot run without these certificates.
|
|
–
|
The Public key must point to a file that contains the certificate, intermediate certificate, and root certificate, concatenated in that order.
|
|
–
|
The Private key file is supplied by the third-party vendor that provided the Public key certificate.
|
|
10.
|
Click Next.
|
Figure 1.12 Configure Database Parameters
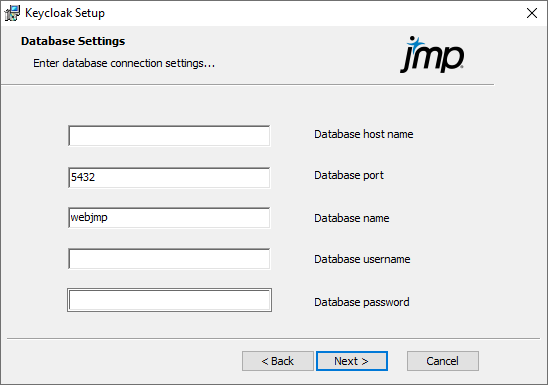
Keycloak stores information about users and clients in a database.
|
11.
|
Specify the database information:
|
Note: The following information should match what you entered when you installed the JMP Live database. See Install the JMP Live Database.
|
–
|
Database host name: Specify the alias or DNS name of the machine with the JMP Live database.
|
|
–
|
Database port: Specify the port that the database listens on.
|
|
–
|
Database name: Specify the name of the JMP Live database.
|
|
–
|
Database username: Specify the user name of the database administrator.
|
|
–
|
Database password: Specify the password of the database administrator.
|
|
12.
|
Click Next.
|
Figure 1.13 Ready to Install Keycloak
|
13.
|
Click Install to proceed.
|
Figure 1.14 Completion Window
|
14.
|
Click Finish.
|
This process can take several minutes, since separate procedures run for Java and Keycloak. You see progress indicators and a command prompt.
If you selected Keycloak to run as a Windows service, Keycloak should be running when the installation finishes. Otherwise, to launch Keycloak manually, use this command:
<your keycloak directory>\bin\kc.bat start --optimized
|
15.
|
Open a browser and navigate to the Keycloak Welcome Page using the HTTP or HTTPS ports that you specified in Figure 1.10. If you chose a default port, this is http://localhost:8888/auth or https://localhost:8443/auth.
|
Figure 1.15 Keycloak Welcome Page
|
16.
|
Click Administration Console.
|
Figure 1.16 Keycloak Administration Console General Options
Refer to the Keycloak manual to set up user access.
|
17.
|
Proceed to Install JMP Live.
|
Install JMP Live
Note: If you have web application firewall (WAF) rules applied to your JMP Live instance, you must disable the SizeRestrictions_BODY rule or JMP Live will not work.
|
1.
|
(Required only if you are using Windows Remote Desktop to install JMP Live, otherwise skip to step 2.) Make sure that the option do not use temporary folders per session is enabled:
|
|
a.
|
On your Windows machine, open a command prompt.
|
|
b.
|
Enter cd %temp%.
|
If you are taken to C:\Users\<user ID>\AppData\Local\Temp\2>, then do not use temporary folders per session is disabled. You need to enable this option before proceeding with the JMP Live installation.
If you are taken to C:\Users\<user ID>\AppData\Local\Temp>, then do not use temporary folders per session is enabled and you can proceed with the JMP Live installation.
|
2.
|
Double-click JMPLive.exe.
|
This file is located in the ZIP file that you downloaded from JMP.
Figure 1.17 Select Your Setup Language
|
3.
|
Select your setup language, and then click Next.
|
Figure 1.18 JMP Live Prerequisites Setup Wizard
|
4.
|
Click Next.
|
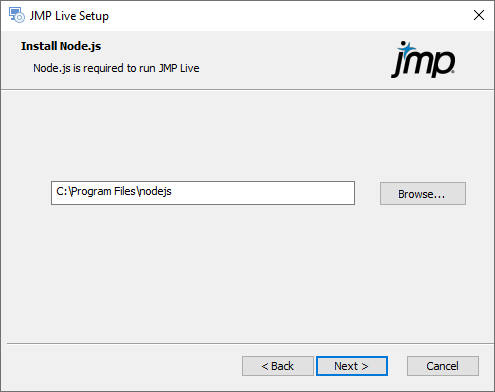
Figure 1.19 Select Installation Path for Node.js
|
5.
|
Specify where to install Node.js:
|
|
–
|
Click Next to accept the default location (recommended).
|
|
–
|
Click Browse to change the default installation folder.
|
Figure 1.20 Select Prerequisites to Install
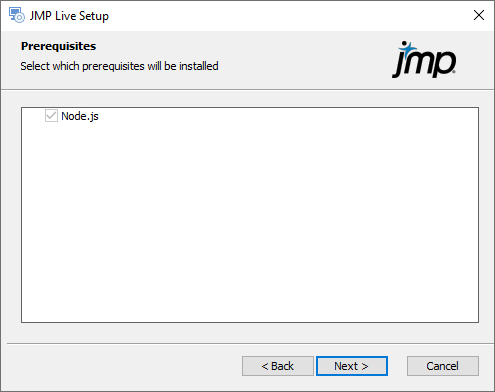
Node.js is selected by default and must be installed.
|
6.
|
Click Next.
|
Figure 1.21 JMP Live Setup Wizard
|
7.
|
Click Next.
|
Figure 1.22 Specify Installation Folder
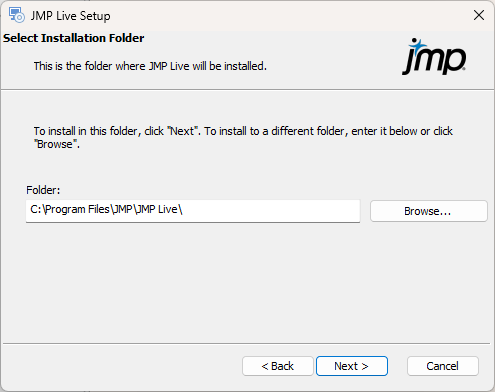
|
8.
|
Specify where to install JMP Live:
|
|
–
|
Click Next to accept the default location (recommended).
|
|
–
|
Click Browse to change the default installation folder.
|
If you change the default location, note the following:
|
–
|
The changed folder contains the JMP Live installation files, but PostgreSQL is always installed in its default location.
|
|
–
|
Since JMP Live can generate log information, make sure that there is adequate disk space in the new location. 1 gigabyte is the recommended minimum.
|
Figure 1.23 Component Selection Window
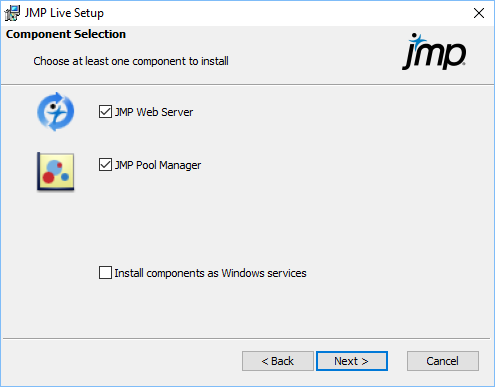
|
9.
|
Select the components that you want to install on this machine (you must select at least one):
|
|
–
|
If you want to install both components on this machine, keep both selected.
|
|
–
|
If you want to distribute the components across different machines, select the component that you want to install on this machine. You must run the installer on the other machine to install the other option.
|
Note: If you are installing for the worker pool architecture, select the JMP Pool Manager component, and skip to step 16. For more information, see About JMP Live Architecture and Authentication.
|
10.
|
(Optional) Choose whether you want to install the selected components as Windows services.
|
If you choose this option, note the following:
|
–
|
JMP Live runs in the background whether you are logged in or not.
|
|
–
|
If a machine is rebooted, the services for JMP Live automatically restart.
|
|
–
|
Information is written to log (text) files instead of to the Windows console. Make sure that there is sufficient space for the log files and regularly delete them to avoid storage issues. Log files are located here (by default):
|
C:\Program Files\JMP\JMP Live\JMPLive\build\daemon\webjmpsvc.out.log
C:\Program Files\JMP\JMP Live\JMPPool\build\daemon\jmppoolsvc.out.log
Figure 1.24 Specify Ports and Database Details
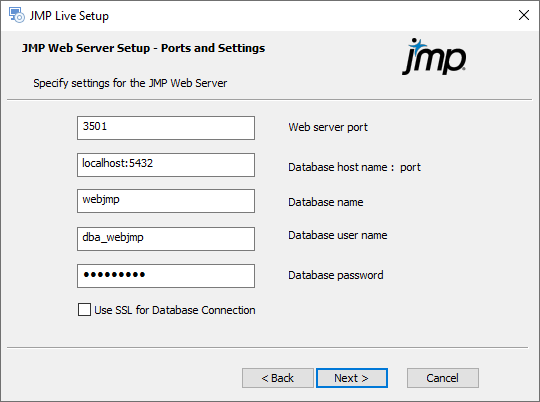
|
11.
|
Specify the following JMP web server settings:
|
|
–
|
Web server port: Enter the HTTPS port that will take requests from a browser. By default, this port is set to 3501. You can specify port 443 (the default HTTPS port), but it is recommended to use a dedicated port for easier monitoring and access control. If you install an application load balancer in front of the web server component, specify this port.
|
|
–
|
Database host name: port:
|
Enter the DNS name of the machine that is running the PostgreSQL database for JMP Live. The default name is localhost (the install machine), but typically this would specify a dedicated server running PostgreSQL. This machine could be within a corporate firewall, outside the firewall, or in a cloud service.
Enter the port that was specified during the installation of PostgreSQL for communication from the outside. The default PostgreSQL port is 5432. See Figure 1.3.
|
–
|
Database name: Enter the name assigned to the JMP Live database within PostgreSQL. It is possible to change this name, but not recommended, as the database installer defaults to webjmp.
|
|
–
|
Database user name and Database password: Enter the administrator user ID and password that you specified while installing the JMP Live Database. The Database user name should be dba_webjmp, but you likely changed the password from the default (which is Password1). Enter that password here.
|
|
–
|
Use SSL for Database Connection: Select this option if your PostgreSQL database requires SSL encrypted communications.
|
Figure 1.25 Create an Administrator Account
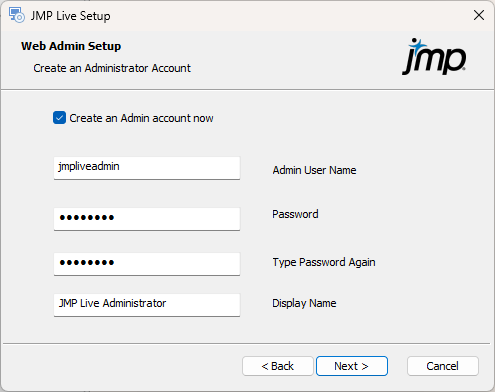
Note: It is strongly recommended that you create an administrator account. However, if you are updating JMP Live from a previous version and already have an administrator account in the database, then you can safely skip this step by deselecting the Create an Admin account now box.
|
12.
|
Enter the administrator user name that you will log on to JMP Live with. Provide a password (default is password) and a display name that will appear when you post content to JMP Live. Note the following:
|
|
–
|
The Admin User Name must not contain spaces and must be lowercase.
|
|
–
|
Once you create an administrator account, you can log on to this account and designate other users as administrators.
|
|
–
|
You can create an administrator account at any time using a command line interface. See Maintain the JMP Live Database.
|
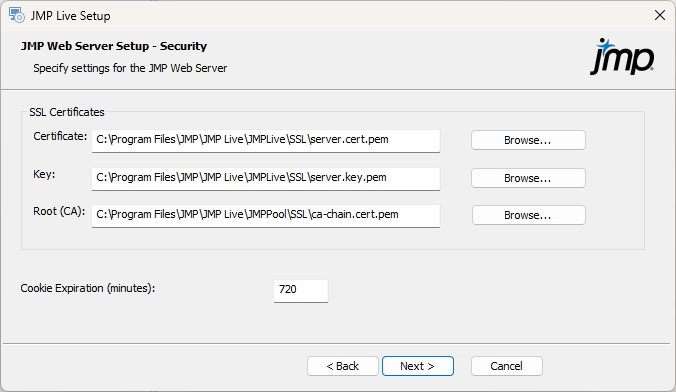
Figure 1.26 Specify SSL Certificates
|
13.
|
Navigate to or enter the SSL certificates for your organization.
|
|
–
|
SSL certificates are text files containing cryptographic keys that enable a browser and the web server to have secure communication. These keys are specific to an organization and are provided by third-party vendors like DigiCert, Symantec, and Network Solutions. JMP Live cannot run without these certificates.
|
|
–
|
The primary certificate and key are configured for the purchaser. The Root (CA) certificate comes from the third-party vendor. If the certificate provider supplies both an intermediate and root certificate, they must be combined into a single file in that order using a text editor. That file should then be specified in the Root (CA) file selection.
|
|
–
|
The JMP Live installer provides a certificate set that allows for minimal testing on a localhost setup. However, it generates warnings when the site is viewed in the local browser, and the site is inaccessible from browsers outside the install machine.
|
Tip: You can validate the SSL certificates after the JMP Live installation is complete. See Validate SSL Certificates for JMP Live. To run the SSL certificate validation utility, from a node.js command line, enter the following directory and command: C:\Program Files\JMP\JMP Live\JMPLive>npm run check-ssl.
|
14.
|
Cookie Expiration: Specify how long the JMP web component remembers that you signed in to JMP Live.
|
|
–
|
The default value is 720 minutes (12 hours) but you can shorten this for increased security.
|
|
–
|
Cookie Expiration is not the same as an idle time-out. You can be using the site constantly, but the cookie expiration forces you to sign in again after it expires.
|
Figure 1.27 Set Up Keycloak
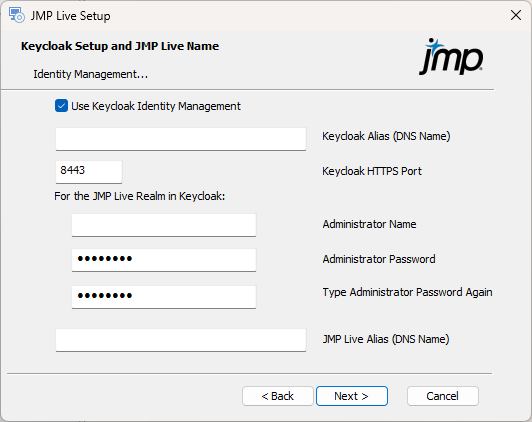
Note: Instead of using Keycloak, it is possible to add a direct connection to Microsoft Active Directory. See Use Active Directory or LDAP. Please be advised that this method will not be supported in future versions of JMP Live.
|
15.
|
Specify the following Keycloak settings:
|
|
–
|
Use Keycloak Identity Management: Enables the Keycloak authentication system. If you deselect this option, Local authentication is used. In this case, users need to create accounts in JMP Live. These users will not be authenticated against different identity providers. For details about connecting Keycloak to your identity provider, see the Keycloak documentation.
|
|
–
|
Keycloak Alias (DNS Name): Specify the name of the server machine that is running the Keycloak authentication service.
|
|
–
|
Keycloak HTTPS Port: Specify the number of the port that Keycloak expects to receive requests on. The default port is 8443.
|
|
–
|
Administrator Name: Specify the administrator name for the JMP Live realm in Keycloak. The realm keeps JMP Live credentials separate from any other software applications that might be using Keycloak authentication.
|
|
–
|
Administrator Password: Specify the administrator password for the JMP Live Keycloak realm.
|
|
–
|
JMP Live Alias (DNS Name): Specify the name of the machine that will be running the main JMP Live site.
|
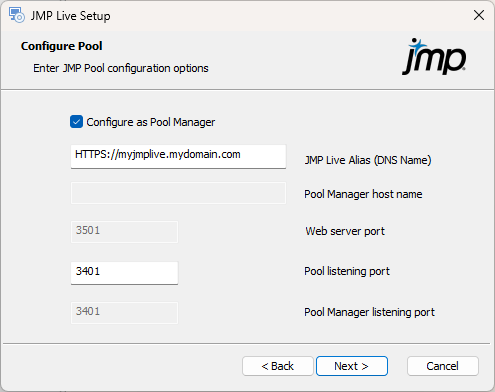
Figure 1.28 Configure the Pool Manager
|
16.
|
If you want to run the Pool Manager on this machine, select the Configure as Pool Manager box:
|
|
–
|
If you are using one machine for all components, or one machine for the Pool Manager and JMP sessions, select this option.
|
|
–
|
If you are using this machine for a worker pool only, do not select this option.
|
|
17.
|
Specify the Pool Manager options:
|
|
–
|
JMP Live Alias (DNS Name): Enter the DNS name, which typically looks like this: machine name.domain name.com/org. Note the following:
|
Unless you are installing all components using the localhost option, you need to specify the web host name.
Even if you have all components on one machine, you likely want to use your organization's SSL certificates for a secure connection. In that case, specify the machine name as the web host name, since the certificates are usually tied to the machine.
|
–
|
Pool Manager host name: (Disabled if you are selected Configure as Pool Manager.) If you are setting up a worker pool on a separate machine, enter the DNS name of the machine that is handling the Pool Manager duties.
|
|
–
|
Web server port: (Disabled if you are installing all components on the same machine, as the port number is already specified in the JMP web component.) If you are installing only the JMP Pool component, enter the port that you used when installing the JMP web component on another machine.
|
|
–
|
Pool listening port: Enter the port that this pool is listening on for communication from the JMP Pool Manager and JMP web components.
|
|
–
|
Pool Manager listening port: (Enabled only if you are configuring a worker pool.) Enter the port that was specified as the Pool listening port for the JMP Pool Manager setup. The worker pool needs to know this port in order to tell the JMP Pool Manager that it is available.
|
Figure 1.29 Configure JMP Settings
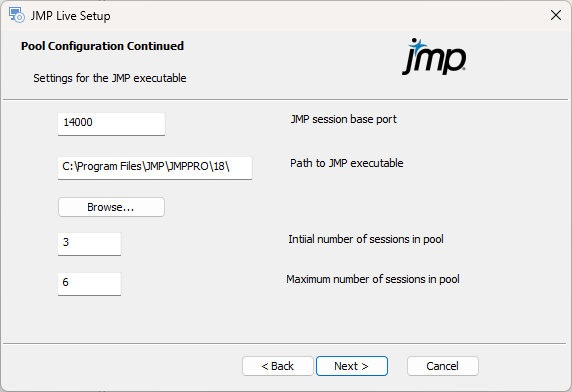
JMP needs to be installed using its own installer on all machines that support creating JMP sessions, whether that is part of the JMP Pool Manager or the worker pool. These sessions of JMP will be started to do work for JMP Live when reports are modified.
|
18.
|
Specify these JMP details:
|
|
–
|
JMP session base port: Enter the base port used by the JMP sessions to talk with the JMP Pool Manager. Each instance of JMP has a unique number starting with this base number.
|
|
–
|
Path to JMP executable: Enter the path to the JMP Pro location. The default installation path appears, so you need to change this only if JMP Pro is located elsewhere.
|
|
–
|
Initial number of sessions in pool: Enter the number of JMP sessions that will be started when the pool is first run.
|
|
–
|
Maximum number of sessions in pool: Enter the upper limit for the number of JMP sessions that are allowed to run on this machine as part of this pool. These sessions are added if the number specified in the initial number of sessions are all in use.
|
Note: If you are installing the Pool Manager, and only want it to handle resource allocation to other worker pools, you can set both the initial and the maximum numbers to zero. In this case, the site will not function until worker pools are configured and running.
Figure 1.30 Configure JMP Settings
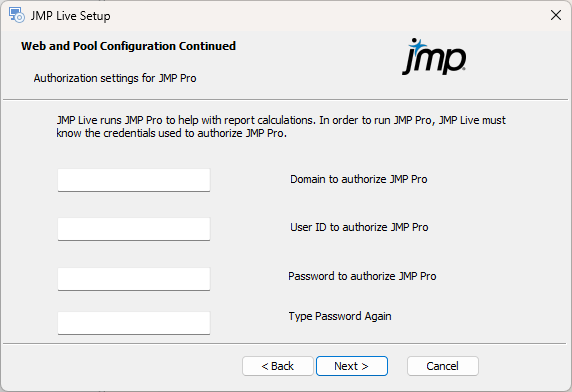
If you chose to install components as Windows services, you see Figure 1.30. If not, proceed to Figure 1.31.
|
19.
|
Specify these credentials for the JMP Pool Service account:
|
|
–
|
Domain to authorize JMP Pro: Enter the network domain of the user that authorizes JMP Pro on this machine. If you are using a local administrative account (such as with Cloud services), specify the host name.
|
Tip: To find the host name, press Windows + r. Type cmd and click OK. Type hostname and press Enter.
|
–
|
User ID to authorize JMP Pro: Enter the user name that authorizes JMP Pro on this machine.
|
|
–
|
Password to authorize JMP Pro: Enter the password that authorizes JMP Pro on this machine for the specified user name.
|
Tip: Keep a note of your user name and password. You will need them to log in and authorize JMP Live for the pool. See Authorize JMP Pro.
|
–
|
Type Password Again: Enter the password again to verify it.
|
Figure 1.31 Configure JMP Settings
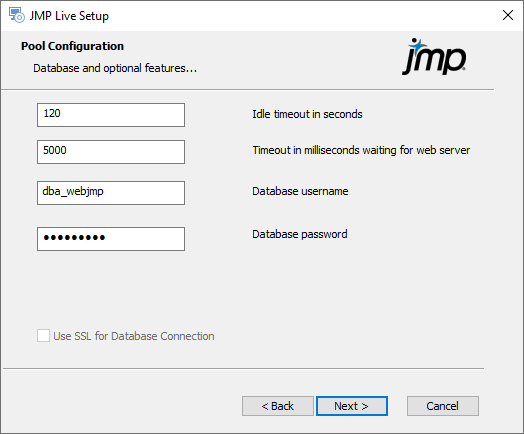
|
20.
|
Specify these JMP details:
|
|
–
|
Idle timeout in seconds: Enter the length of time that a JMP instance waits for additional work before dropping the connection with the JMP web component and waiting for a new request.
|
|
–
|
Timeout in milliseconds waiting for web server: Enter how long an instance waits for further communication during an existing transaction before it gives up and discards the existing work request.
|
|
–
|
Database username: Specify the user name of the database administrator.
|
|
–
|
Database password: Specify the password of the database administrator.
|
|
–
|
SSL Root Certificate: (Appears if you are installing the JMP Pool Manager component only) Specify the location of your organization’s certificate authority file.
|
Figure 1.32 Start JMP Live Installation
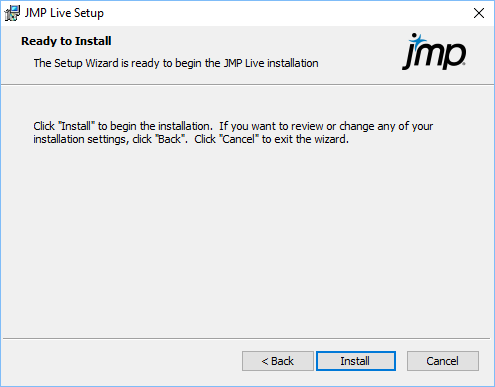
|
21.
|
Click Install to start the JMP Live installation, and Finish once the installer is done.
|
JMP Live should automatically connect to Keycloak, and you should be able to log in to JMP Live using the JMP Live alias that you provided in step 15. If you have problems logging in to JMP Live, you might need to connect manually. See Manually Connect Keycloak and Start JMP Live.
|
22.
|
Proceed to authorize JMP Pro. See Authorize JMP Pro.
|
Tip: After you authorize JMP Pro, you can add users or groups to JMP Live by importing them from your Active Directory. For details, see the JMP Live Help.
Authorize JMP Pro
After you install JMP Pro and JMP Live, you must authorize JMP Pro for the JMP Pool Service. After the initial authorization, you must re-authorize JMP periodically. You can find the date by which you need to re-authorize by in JMP Live under Admin > Server.
Tip: It is best to re-authorize during non-peak usage times. Re-authorizing might cause a short amount of pool downtime.
To authorize or re-authorize JMP Pro
|
1.
|
Log in to the machine running the JMP Pool Service:
|
|
–
|
If you are running the JMP Pool as a Windows service, log in as the user that activated JMP Pro. This should be the same user that is running as the Windows service.
|
|
–
|
If you are running the JMP Pool using the Windows command line, log in as the user that authorized JMP Pro.
|
|
2.
|
(Perform this step only if you are re-authorizing before the re-authorization date.)
|
|
a.
|
Navigate to the Windows registry. Click the Windows icon and type Registry Editor.
|
|
b.
|
Delete this folder from the registry: Computer\HKEY_CURRENT_USER\SOFTWARE\JMP\JMPPRO\18.0\License
|
|
3.
|
Open the jmp.exe file, installed here (by default): C:\Program Files\JMP\JMPPro\18.
|
|
4.
|
Follow the authorization prompts until JMP Pro opens, then you can close JMP.
|
|
5.
|
In JMP Live, click Admin > Pool. Click Terminate all
 to force all JMP sessions to reload. to force all JMP sessions to reload. |
(Optional) Configure Advanced Settings
During the JMP Live installation, you specify certain settings. To change these settings later, or add to the advanced settings, update the environment (.env) files. The JMP Live and JMP Pool Manager components each have their own environment file here (by default):
|
•
|
C:\Program Files\JMP\JMP Live\JMPLive
|
|
•
|
C:\Program Files\JMP\JMP Live\JMPPool
|
Caution: Make changes to environment files with caution, as even a small mistake could cause JMP Live to fail.
Once you update the environment file, you need to restart the component for the changes to take effect. For details about how to restart components, see Manually Connect Keycloak and Start JMP Live.
JMP Live Environment File Settings
ADMIN_LANG
(Optional) Sets the language that appears when using CLI tools. Options include de (German), en (English), es (Spanish), fr (French), it (Italian), ja (Japanese), ko (Korean), and zh-CN (Chinese).
APIKEY_ENABLED
(Optional, Boolean) Specifies whether users need a key to access the JMP Live APIs using JSL. Users can get an API key through their user profile in JMP Live. The default is 1 (enabled).
AUTH_SCHEME
(Required) Authentication scheme that the JMP web component uses. Possible values are keycloak, ldap, and local. This should be set once for a given JMP Server instance and never changed unless starting over with an empty database.
CIPHERS
(Optional) Specify allowed ciphers in an unquoted, comma-separated list. By default, JMP Live allows these ciphers:
|
–
|
TLS_AES_128_GCM_SHA256
|
|
–
|
TLS_AES_256_GCM_SHA384
|
|
–
|
TLS_AES_128_CCM_SHA256
|
|
–
|
TLS_AES_128_CCM_8_SHA256
|
|
–
|
ECDHE-RSA-AES128-GCM-SHA256
|
|
–
|
ECDHE-ECDSA-AES128-GCM-SHA256
|
|
–
|
ECDHE-RSA-AES256-GCM-SHA384
|
|
–
|
ECDHE-ECDSA-AES256-GCM-SHA384
|
To allow only a subset of these ciphers, provide a comma-separated list. For example:
CIPHERS=TLS_AES_128_GCM_SHA256,TLS_AES_256_GCM_SHA384,TLS_AES_128_CCM_SHA256,TLS_AES_128_CCM_8_SHA256
COOKIE_EXPIRE_MINUTES
(Optional) Length of time in minutes that a session cookie is valid. If both _MINUTES and _SECONDS are specified, the one that specifies the longer amount of time is used. The default value is 720 minutes (12 hours).
COOKIE_EXPIRE_SECONDS
(Optional) Length of time in seconds that a session cookie is valid. If both _MINUTES and _SECONDS are specified, the one that specifies the longer amount of time is used. If you want to use COOKIE_EXPIRE_SECONDS, you should set COOKIE_EXPIRE_MINUTES to 0. The default value and the minimum expiration allowed are five seconds.
COOKIE_SAMESITE_NONE
(Optional) Specifies the Cookie SameSite attribute value used by JMP Live.
|
–
|
If you want to embed JMP Live content in other applications, setting the value to Lax (0) prevents that from working. This is the default value.
|
|
–
|
Setting the value to None (1) might allow embedding to work if browser settings do not otherwise prevent it.
|
COOKIE_SECRET
(Required) Secret used for computing the hash for session cookies for this instance of JMP Live.
DB_DATABASE
(Required) Name of the PostgreSQL database on DB_HOST to use. Normally, it is webjmp.
DB_HOST
(Required) Host name of the machine where the PostgreSQL database is running. The format is host-name:port. Port must be included.
DB_MAX_CONN_JMP_LIVE
The maximum number of concurrent database connections that any one instance of JMP Live attempts to sustain. The default value is 25. When determining a value for this setting, please remember:
|
–
|
The database itself has a max_connections budget (defined in postgresql.conf) that you should not exceed.
|
|
–
|
There can be more than one instance of JMP Live running in a cluster.
|
|
–
|
The max_connections budget needs to be shared between JMP Live and JMP Pool (a split of 80% to 20% is recommended).
|
DB_PASSWORD
(Required) Password that DB_USERNAME uses to connect to PostgreSQL.
DB_SSL_CA_FILE
(Optional) Relative path to the certificate authority file for running in secure SSL mode.
DB_SSL_CERT_FILE
(Optional) Relative path to the client certificate public key file when using two-way SSL authentication.
DB_SSL_INSECURE
(Optional) Determines whether PostgreSQL validates that the client certificate is signed by a trusted authority. The default value is 0, which means validation is performed. To not perform validation, set this value to 1.
DB_SSL_KEY_FILE
(Optional) Relative path to the client certificate private key file when using two-way SSL authentication.
DB_SSL_ON
(Optional) Specifies whether the JMP Live connection to PostgreSQL is required to use SSL. The default value is 0, which means the JMP Live connection is not required to use SSL. To require the use of SSL, set this value to 1.
DB_USERNAME
(Required) User name of the PostgreSQL user. Normally, it is dba_webjmp.
DEBUG_DEV
(Optional) List of comma-separated string values that determine which debug statements in the code are active and which are not. There is no default value.
DEBUG_DEPTH
(Optional) Determines the depth to which objects are sent to the log in a debug statement (for example: debug('This is my object: %O', myObject);). The default value is 10.
JMPLIVE_BASEURL
(Required) The URL that components such as the JMP Pool and Keycloak use to communicate with the JMP Live website.
LOG_HTTPHEADERS
(Optional, Boolean) Determines whether HTTP headers are included in pretty-printed log records of HTTP requests. The default value is 0 (off, no headers are included).
LOG_LEVEL
Optional) Sets the lowest level of Bunyan logger messages that are active in this JMP Server instance. These are the messages that go to Loggly. Possible values include trace, debug, info, warn, error, or fatal. The logger lines in the code look like "logger.debug(...);". The default value is info.
LOG_PRETTY
(Optional, Boolean) Determines whether the Bunyan logging in the console stream displays as raw JSON (0) or is pretty printed (1). This affects only the console stream; the Loggly stream is always raw JSON. The default value is 0 (raw JSON).
LOGGLY_SUBDOMAIN
(Optional) Sets the subdomain to send log records to Loggly.
LOGGLY_TOKEN
(Optional) Sets the token to use when sending log records to Loggly.
NODE_ENV
(Required) Set this to production. This is the correct mode for the JMP Server.
PORT
(Required) HTTPS port that this instance of JMP Live is running on.
SESSION_TICKET_EXPIRE_HOURS
(Optional) The number of hours to retain JMP session ticket records in the Tickets table. This is for JMP sessions, not log on sessions. If both _MINUTES and _HOURS are specified, the one that specifies the longer amount of time is used. The default value is 24 hours.
SESSION_TICKET_EXPIRE_MINUTES
(Optional) Number of minutes to retain JMP session ticket records in the Tickets table before they are removed. This is for JMP sessions, not log on sessions. The default value is 1440 minutes (24 hours).
SESSION_PURGE_INTERVAL_MINUTES
(Optional) Frequency (in minutes) at which expired sessions are purged from the database. If both _MINUTES and _SECONDS are specified, the one that specifies the longer amount of time is used. The default value is 15 minutes.
SESSION_PURGE_INTERVAL_SECONDS
(Optional) Frequency (in seconds) at which expired sessions are purged from the database. If both _MINUTES and _SECONDS are specified, the one that specifies the longer amount of time is used. If you want to use SESSION_PURGE_INTERVAL_SECONDS, you should set SESSION_PURGE_INTERVAL_MINUTES to 0. The default value and the minimum purge interval allowed are five minutes.
SSL_CA_FILE
(Optional) Relative path to the certificate authority file.
SSL_CERT_FILE
(Optional) Relative path to the certificate file.
SSL_KEY_FILE
(Optional) Relative path to the certificate key file.
JMP Pool Environment File Settings
APPLYPACKAGEPREFS
(Optional, Boolean) Determines whether preferences stored with the package are applied on the server. Specify 0 for false and 1 for true. The default value is true (1).
DB_MAX_CONN_JMP_POOL
The maximum number of concurrent database connections that this JMP Pool attempts to sustain. The default value is 10. When determining a value for this setting, please remember:
|
–
|
The database itself has a max_connections budget (defined in postgresql.conf) that you should not exceed.
|
|
–
|
There can be more than one JMP Pool.
|
|
–
|
The max_connections budget needs to be shared between JMP Live and JMP Pool (a split of 80% to 20% is recommended).
|
DB_PASSWORD
(Required) Password for logging in to the PostgreSQL database.
DB_SSL_CA_FILE
(Optional) Relative path to the certificate authority file for running in secure SSL mode.
DB_SSL_CERT_FILE
(Optional) Relative path to the client certificate public key file when using two-way SSL authentication.
DB_SSL_INSECURE
(Optional) Determines whether PostgreSQL validates that the client certificate is signed by a trusted authority. The default value is 0, which means validation is performed. To not perform validation, set this value to 1.
DB_SSL_KEY_FILE
(Optional) Relative path to the client certificate private key file when using two-way SSL authentication.
DB_SSL_ON
(Optional) Specifies whether the JMP Live connection to PostgreSQL is required to use SSL. The default value is 0, which means the JMP Live connection is not required to use SSL. To require the use of SSL, set this value to 1.
DB_USERNAME
(Required) User name for logging in to the PostgreSQL database.
DEBUG
(Optional) List of comma-separated string values that determine which debug statements in the code are active and which are not. There is no default value.
HOST
(Optional) Host name of this JMP Pool. The default host name is os.hostname().
INITIAL_JMP_PROCESSES
(Optional) Number of JMP sessions that will be started to help recalculate reports when they are explored on the website. The default value is 4 sessions.
IS_MANAGER
(Optional, Boolean) Specifies if this pool is the pool manager. If it is, set this to 1.
JMP_BASE_PORT
(Required) Start of a range of ports that JMP sessions listen on.
JMP_INSTALLDIR
(Optional) Tells JMP Live where the JMP desktop application is installed.
JMP_LOGSTART
(Optional) Creates a log of JMP start-up, such as where JMP is getting license and preference information from.
JMP_PATH
(Required) Path to the JMP executable.
JMP_SERVER_IDLE_TIMEOUT
(Optional) Amount of time (in seconds) a committed JMP server can remain idle before being recycled. The default value is 120 seconds.
JMPLIVE_BASEURL
(Used only if this is the pool manager.) The URL that components such as the JMP Pool and Keycloak use to communicate with the JMP Live website.
LOAD_JMP_ADDINS
Determines whether JMP add-ins are loaded when JMP starts. The default value is 1, which means add-ins are loaded. To prevent add-ins from loading, set this value to 0.
LOG_LEVEL
Optional) Sets the lowest level of Bunyan logger messages that are active in this JMP Server instance. These are the messages that go to Loggly. Possible values include trace, debug, info, warn, error, or fatal. The logger lines in the code look like "logger.debug(...);". The default value is info.
LOG_PRETTY
(Optional, Boolean) Determines whether the Bunyan logging in the console stream displays as raw JSON (0) or is pretty printed (1). This affects only the console stream; the Loggly stream is always raw JSON. The default value is 0 (raw JSON).
MAX_JMP_PROCESSES
(Optional) Maximum number of JMP processes that will be launched based on demand (an elastic JMPPool). The default value is specified in INITIAL_JMP_PROCESSES.
NODE_ENV
(Required) Set this to production. This is the correct mode for the JMP Server.
POOL_MANAGER_HOST
(Used only if this is not the pool manager, so it can find the pool manager.) The DNS name of the machine running the pool manager process. The default value is localhost.
POOL_MANAGER_PORT
(Used only if this is not the pool manager.) Port that the pool manager uses to communicate with worker pool instances. The default port is PORT.
PORT
(Required) Port that this JMP Pool is listening on.
SSL_CA_FILE
(Optional) Relative path to the certificate authority file.
WEBJMP_RETRY_WAIT
(Used only if this is the pool manager.) Number of milliseconds JMP waits before trying to reconnect to the JMP web component. The default value is 5000 milliseconds.
Migration Notes
If you are migrating from a previous version of JMP Live to 18, note the following differences in how JMP Live implements certain features:
|
Scenarios
|
Previous behavior
|
JMP Live 18 behavior
|
|---|---|---|
|
You use a password-protected SMTP server.
|
The password is stored in the database and not encrypted.
|
The password is now encrypted. After upgrading, you must re-enter your SMTP password in the Admin > Settings > E-mail Settings section of JMP Live.
|
|
You have a flagged user or post.
|
The user or post is flagged.
|
Flagged users or posts are no longer supported in 18. Any flagged users or posts are approved.
|
|
You have allowed downloading permission for members in a space, but disallowed downloading on individual posts in the space.
|
The individual post cannot be downloaded.
|
Disallowing downloads on an individual post is no longer supported in 18. In a space where members can download posts, any previously disallowed posts can be downloaded.
|
|
A user is given Create, Edit, Replace, or Delete permission.
|
All of these four individual permissions were supported.
|
There is one permission that allows creating, editing, replacing, or deleting posts, called Contribute permission.
|
|
You want to create new a JMP Live report using JSL.
|
Use the command New Web Report.
|
Use the command New JMP Live Content.
|
About JMP Live Architecture and Authentication
If you are installing the JMP Live server on-premises, you should understand the architecture of the JMP Live system and possible configurations for authentication with third-party identity providers.
Architecture Overview
JMP Live consists of several modules communicating with each other. This architecture makes it possible to distribute the workload across different computing resources to handle larger request loads.
Figure 1.33 JMP Live Architecture
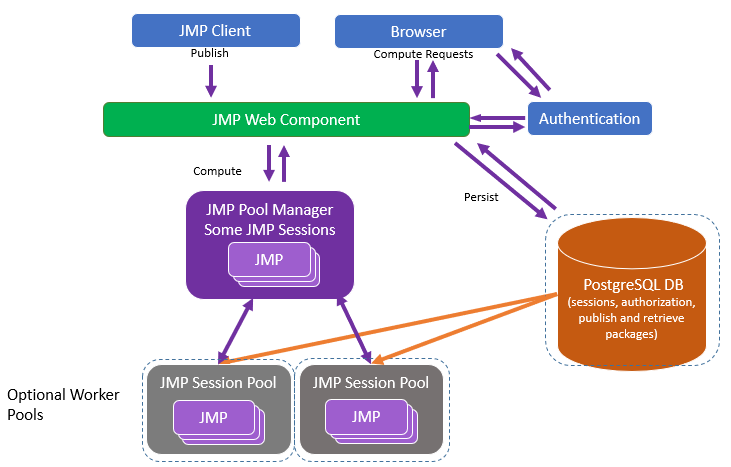
You can run JMP Live on a single computing resource, but this setup is not recommended. The recommended setup is to keep the database separate from the other components of JMP Live, and to give the database a dedicated computing instance that is frequently backed up to ensure the safety of the JMP Live content. The database can be on a hosted service, and the rest of the components can be hosted in on-premises resources. In that scenario, you would not use the JMP Live Database Installer, but would need to set up a PostgreSQL 14.5 compatible instance on the hosted service. Follow the instructions in Install JMP Live Using an Existing Database.
Determine the Installation Size
Determining the size of the installation is challenging, since there can be unknown factors at individual installation sites that can impact performance. Network speed is an important factor, and the decision to use dedicated machines or virtual machines also impacts performance. JMP cannot guarantee that any of the configurations described here will perform well at every location.
The main criterion when considering possible installation size is the number of users:
|
•
|
A small deployment is considered to be 100 users.
|
|
•
|
A medium deployment is considered to be 500 users.
|
|
•
|
A large deployment is considered to be 2,000 users.
|
In all cases, it is assumed that every user uses the site occasionally and are looking at a variety of reports with fairly distributed usage. Occasional usage might be 10 times per day.
|
•
|
If you have users that heavily use the site constantly, you will need a much more robust setup.
|
|
•
|
If you have users frequently accessing just a few reports, then both the robustness of the computing resource dedicated to the JMP web component and the database will be important.
|
Small Deployment
In a small JMP Live deployment (such as 100 users), it is possible to install everything except the database on a single dedicated machine.
Figure 1.34 Recommended Configuration for a Small Deployment
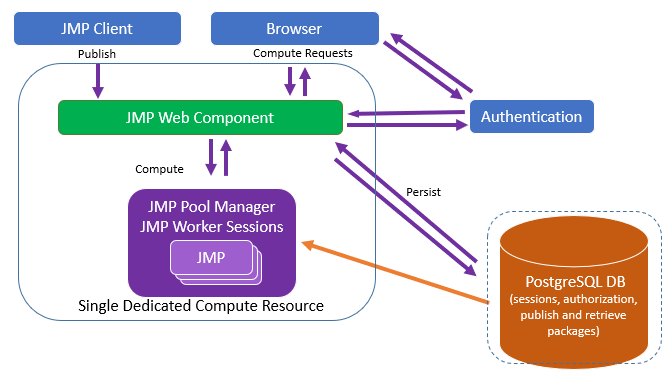
In this scenario, the JMP web and the JMP Pool components are installed on the same machine. During the installation, select the option to Configure as Pool Manager. The number of JMP instances associated with this JMP Pool Manager are the total number of JMP instances that are run for the site.
For the capabilities of this computing resource, more is always better, and much depends on the processor type, network speeds, and so on. An absolute minimum to consider is a 4-core machine with at least 16 gigabytes of dedicated RAM. The amount of storage is most important for the database and depends on the number of reports stored. One terabyte of storage is the minimum.
Medium Deployment
In a medium JMP Live deployment (such as 500 users), there are two configurations that you can consider, based on the type of reports that are being retrieved:
|
•
|
If you have a high number of report retrievals, but the reports themselves do not contain data filters or the need to recompute the statistics, then the primary area of concern is the JMP web component.
|
|
•
|
If there are a lot of report computations required, then the primary area of concern is the JMP Pool Manager.
|
In cases where the JMP web component is of primary importance, or if you do not know whether you will have a compute-intensive environment, the recommended configuration is below.
Figure 1.35 Recommended Configuration for a Medium Deployment
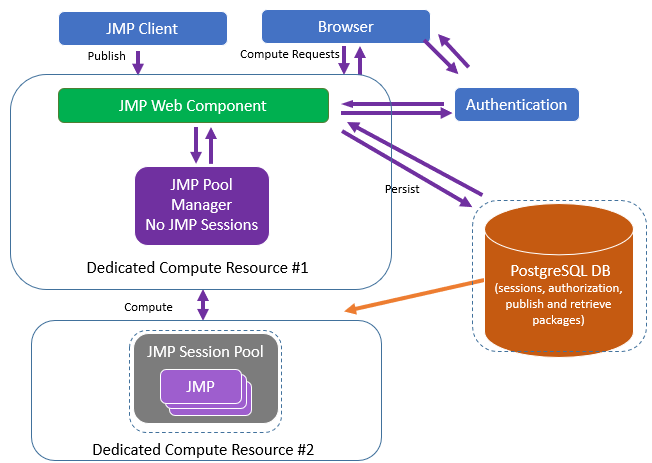
In a standard configuration where the JMP web component needs optimum performance, the JMP Pool Manager does not have JMP sessions of its own. You set the number of JMP sessions in the JMP Pool Manager to zero. All JMP sessions reside on the second computing resource, the JMP Session Pool.
If you need a more compute-intensive environment, then assign sessions to the JMP Pool Manager (perhaps five). This might reduce the performance of the JMP web component, but provides additional computing capacity for reports.
Large Deployment
In a large JMP Live deployment (such as 2,000 users), you might need multiple JMP Session Pools and a separate dedicated computing resource for the JMP Pool Manager.
Figure 1.36 Recommended Configuration for a Large Deployment
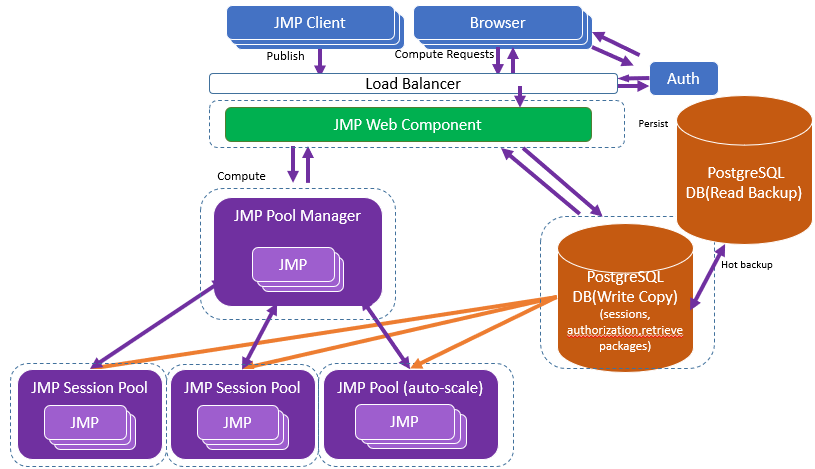
The JMP web component, JMP Pool Manager component, JMP Session Pools, and PostgreSQL databases are all dedicated instances. The number of JMP sessions that you can have depends on the computing power and memory capacity of each instance.
Here are some suggestions for each instance:
|
•
|
JMP web component and JMP Session Pool instances: A suggested minimum of 4-core machines, but preferably 8-core machines with 32 gigabytes of RAM.
|
|
•
|
JMP Pool Manager: A suggested minimum of a 4-core machine with 16 gigabytes of RAM.
|
|
•
|
PostgreSQL databases: The machines should anticipate the storage requirements based on the volume of publishing for your organization. A scalable instance would be best, otherwise 5 terabytes of storage is a suggested minimum.
|
The following elements are also suggested:
|
•
|
A load balancer to provide a single entry point to handle the security of HTTP and HTTPS requests.
|
|
•
|
A read backup of the PostgreSQL database to provide a quick switchover in the event of a failure or connectivity issue with the primary database. The backup should be updated frequently.
|
Considerations for Hosting Services
For some hosting services like Amazon Web Services or Microsoft Azure, it is possible to set up auto-scaling for the JMP Session Pools. This works as follows:
|
1.
|
A trigger, like a time of day or a CPU utilization on a Session Pool node, can cause an additional computing resource to be started.
|
|
2.
|
The JMP Session Pool on the newly started resource reports to the Pool Manager when it becomes live.
|
To use auto-scaling, during installation of the Session Pool on the image that will be replicated during scaling, you must have selected the option to install components as Windows services. This automatically starts the Session Pool component when the computing instance is instantiated. The Session Pool reports to the Pool Manager and registers its availability to provide computing services.
Authentication Considerations
The facilities that JMP Live provides for authentication are based on the location of the installation. For an on-premises installation, JMP Live can connect to a Microsoft Active Directory endpoint if your organization supports Active Directory or LDAP (Lightweight Directory Access Protocol).
The authentication mechanisms covered here relate to how JMP Live connects to the user's identity providers. Communication between JMP and JMP Live is different.
Figure 1.37 JMP Live Authentication Options and Flow
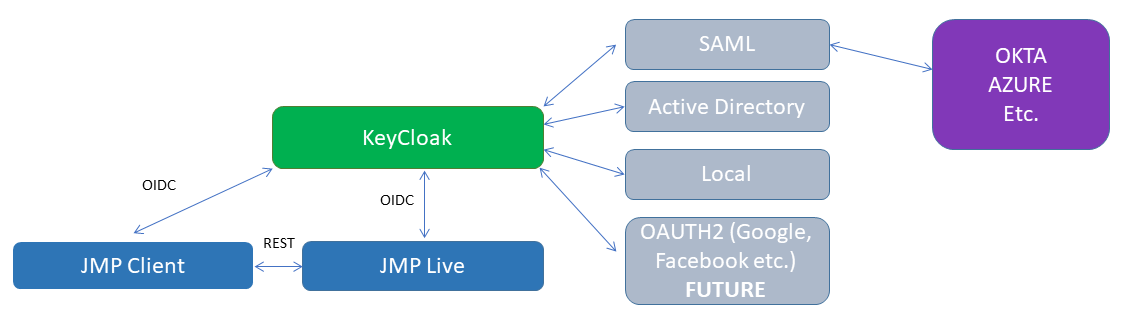
Keycloak Application
The Keycloak application acts as a bridge to various authentication mechanisms. OpenID Connect (OIDC) is used between the JMP Client, JMP Live, and Keycloak to secure those transactions. The connection between Keycloak and the various authentication mechanisms depends on that mechanism, but it is often TLS.
Keycloak provides authentication session tokens to JMP Live and JMP. These tokens indicate whether the user is allowed to use JMP Live. The tokens also tell JMP Live when the authentication session has expired.
Use Active Directory or LDAP
To enable on-premises authentication using Active Directory or LDAP, you need to specify certain parameters in the environment file for the JMP web component.
|
1.
|
Open the environment file for the JMP web component, located here (by default): C:\Program Files\JMP\JMP Live\JMPLive\.env.
|
|
2.
|
If you have installed the JMP web component as a Windows service, use the Task Manager to stop the service before you update the environment file.
|
|
3.
|
Specify these parameters in the .env file:
|
AUTH_SCHEME=ldap
This specifies the authentication method as LDAP or Active Directory.
LDAP_URL="ldap://site_ldap_endpoint.mycompany.com:port#"
This is the communication endpoint for the Active Directory requests, where port# is the 4-digit port used for the Active Directory communications. The connection must be direct to the Active Directory or LDAP instance.
LDAP_BIND_DN="CN=COMPANY LDAP-Read,OU=Generic and Shared Accounts,OU=Admin,DC=mydepartment,DC=mycompany,DC=com"
This is the administrator account for the Active Directory binding. This is site specific. If your site does not allow for anonymous binding, this might be a domain-specific account.
LDAP_SEARCH_BASE="DC= mydepartment,DC= mycompany,DC=com"
This is the base domain from which to search for users by user name.
LDAP_BIND_CRED="abcd1234efgh"
This is the administrator account password
LDAP_SEARCH_FILTER=(samAccountName={{username}})(memberOF=CN=JMP Live User Group,OU=Groups,DC=mydepartment,DC=mycompany,DC=com))
The filter used to search for the user. The user name in {{}} is interpolated as the provided user name. You can use the memberOF option to validate that a user is in the group.
|
4.
|
Save the .env file.
|
|
5.
|
If you have installed the JMP web component as a Windows service, use the Task Manager to restart the service once you finish updating the environment file.
|
Validate SSL Certificates for JMP Live
After the JMP Live installation is complete, you can validate the SSL certificates. An example using the installation defaults is as follows:
|
1.
|
Go to the Windows Start Menu and open a Node.js command prompt.
|
|
2.
|
Go to the JMPLive folder, located here (by default): C:\Program Files\JMP\JMP Live\JMPLive.
|
|
3.
|
Enter the following command:
|
npm run check-ssl
Example
C:\Users\userid>cd C:\Program Files\JMP\JMP Live\JMPLive
C:\Program Files\JMP\JMP Live\JMPLive>npm run check-ssl
> jmplive@18.0.0 check-ssl
> node ./config/checkSSL.js
The certificate was read correctly.
The private key was read correctly.
The certificate authority was read correctly.
Certificate start date: 03/02/2024
Certificate expiration date: 17/03/2024
The public certificate and private key match correctly.
The certificate was issued by the provided certificate authority.
C:\Program Files\JMP\JMP Live\JMPLive>
Manually Connect Keycloak and Start JMP Live
After you install JMP Pro, the JMP Live Database, Keycloak and JMP Live, JMP Live and Keycloak should be automatically connected. If you have problems logging in to JMP Live after the installation, you might need to connect to Keycloak and start JMP Live manually.
|
1.
|
If you are using the JMP Live database as the Keycloak database, run JMP Live once.
|
This populates the JMP Live database with the correct schemas and tables for Keycloak to operate.
|
2.
|
If JMP Live is running as a Windows service, stop it:
|
|
a.
|
Type Task Manager in the Windows search bar. Or, press Ctrl+Alt+Delete and select Task Manager.
|
|
b.
|
Click the Services tab.
|
Tip: If you do not see the Services tab, you might need to click More Details.
|
c.
|
Right-click webjmpsvc.exe and jmppoolsvc.exe and click Stop.
|
|
3.
|
Type Command Prompt in the Windows search bar. Run the command prompt as an administrator (right-click Command Prompt and choose Run as administrator).
|
|
4.
|
Navigate to the JMPLive component installation directory. Enter: cd C:\Program Files\JMP\JMP Live\JMPLive (assuming that JMP Live is in the default directory).
|
|
5.
|
Edit the .env file using Notepad. Enter: start Notepad .env.
|
|
6.
|
In the .env file, verify the parameters in these lines:
|
AUTH_SCHEME=keycloak
Note: Alternative choices include ldap and local. ldap is the legacy choice to connect to LDAP or the Microsoft Active Directory (do not choose this option unless you are using JMP 15.0 or higher). local allows for a standalone authentication without connecting to an identity provider.
KEYCLOAK_SERVER_URL=https://mykeycloakserver.mydomain.com:8443
Where mykeycloakserver.mydomain.com:8443 is the URL of your Keycloak server and the port that allows HTTPS access.
KEYCLOAK_ADMIN=keycloakadmin
Where keycloakadmin is the administrator name for the JMP Live realm in Keycloak.
KEYCLOAK_ADMIN_CREDENTIALS=Password1
Where Password1 is administrator password for the JMP Live Keycloak realm.
JMPLIVE_BASEURL=https://myjmpliveinstance.mydomain.com:3501
Where myjmpliveinstance.mydomain.com:3501 is the DNS name or alias of your JMP Live server and the port that you are using for HTTPS access.
|
7.
|
Save the .env file updates. Click File > Save.
|
|
8.
|
Start the JMP Live components:
|
|
–
|
If you installed JMP Live as a Windows service, open the Task Manager, Services tab (refer to step 2) and start each JMP Live service. Right-click webjmpsvc.exe and jmppoolsvc.exe and click Start.
|
|
–
|
If you have not installed JMP Live as a Windows service, perform the steps under Components Not Installed as Windows Services.
|
JMP Live and Keycloak should now be working together.
Components Not Installed as Windows Services
|
1.
|
Go to the directory where JMP Live is installed. By default, JMP Live is installed here: C:\Program Files\JMP\JMP Live\JMPLive.
|
|
2.
|
Double-click the launch.cmd file. This starts any components installed on this machine.
|
|
3.
|
If the installation has been distributed across several machines, repeat step 2 on each machine.
|
A command prompt for each component starts, showing the operation status of each component.
Tip: To stop the components, press Ctrl+Break or Ctrl+C.
Enable or Disable Publishing to JMP Live
JMP Live is a website purchased and hosted by your company for private sharing of JMP content. JMP Public is a public instance of JMP Live that anyone can share JMP content to.
You can manage publishing settings by creating a jmpStartAdmin.jsl file.
Enable or Disable Publishing to JMP Live
Administrators can enable or disable publishing to JMP Live for specific URLs. On a user’s PC, the administrator can specify the URLs in a jmpStartAdmin.jsl file.
Enable JMP Live URL() specifies the URLs that users can publish to. For example:
Enable JMP Live URL( "https://public.jmp.com" ) // enables publishing to the JMP Public URL
Disable JMP Live URL() specifies the URLs that users cannot publish to. For example:
Disable JMP Live URL( "https://public.jmp.com" ) // disables publishing to the JMP Public URL
Note: If a URL appears in both lists, publishing to the URL is disabled.
You can use an asterisk as a wildcard to specify URLs:
|
•
|
* (any URL)
|
|
•
|
*.jmp.com (a URL that ends in jmp.com)
|
|
•
|
https://public.* (a URL that starts with https://public.)
|
|
•
|
*public* (a URL that contains public)
|
Update Code Modules
Much of JMP Live is developed using JavaScript. Node.js provides the coding ecosystem for the web server and much of the other infrastructure that JMP Live needs to run. This ecosystem contains numerous independently developed software applications to achieve specific functions. Occasionally, these modules might need to be updated with security fixes. This can also become part of a periodic, automated process. JMP always updates the code modules when distributing a new release of JMP Live, but the module update can provide interim security fixes.
To update the code modules, you must run the Node Package Manager (npm) from a Windows command prompt. To do this manually,
|
1.
|
Go to the Windows Start Menu and look under Node.js.
|
|
2.
|
Start a Node.js command prompt with administrator privileges.
|
|
3.
|
To have npm update any packages with security packages, run the following command inside the JMPLive and JMPPool directories:
|
npm audit fix
You can also prefix the fixes that will be applied in the above operation using this command:
npm audit fix --dry-run
If you want the output in a JSON format, append --json to the --dry-run command line.
Uninstall Windows Services
If you decide that you want to remove the Windows services but keep JMP Live installed, you can run the uninstall_services.cmd file in the main application directory. Similarly, you run the install_services.cmd file to re-install the Windows services. These files exist only if you selected the option during installation to install as Windows services.
Maintain the JMP Live Database
As a JMP Live administrator, in order to maintain the JMP Live Database, you should be familiar with the following aspects of the PostgreSQL database:
Backup and Restore
It is strongly recommended for JMP Live administrators to familiarize themselves with backup and restore capabilities in PostgreSQL, and to plan and implement a backup and restore strategy.
For more information, see https://www.postgresql.org/docs/14/backup.html.
Routine Database Maintenance Tasks
It is recommended for JMP Live administrators to familiarize themselves with database maintenance capabilities in PostgreSQL, and to plan and implement a maintenance routine.
For more information, see https://www.postgresql.org/docs/14/maintenance.html.
Caution: If your JMP Live version is lower than 15.2, do not execute vacuumlo.exe. Prior to version 15.2, this was an unsafe operation.
JMP Live Database Connection Pool
The JMP Live Database cannot accept an infinite number of connections - that is, it cannot satisfy an infinite number of requests at the same time. The database itself has a maximum number of connections that is defined by the max_connections value in the postgresql.conf file. If you used a JMP Live installer to install your PostgreSQL database, then this value is set to 500 by default. You can think of this value as your overall budget for database connections. You have control over the size of your budget, and how you spend it.
Change the size of your budget
The size of your budget is defined by the max_connections value in the postgresql.conf file. To change it, simply change the max_connections value and restart the PostgreSQL service. Keep in mind that connections are not free; they come with a cost in-memory usage. For guidance, refer to the PostgreSQL documentation and other trusted sources.
Change how you spend your budget
You have control over two values:
|
•
|
The value of DB_MAX_CONN_JMP_LIVE in C:\Program Files\JMP\JMP Live\JMPLive\.env.
|
|
–
|
This value represents the maximum number of concurrent database connections that a single instance JMP Live attempts to sustain.
|
|
–
|
Basic tips for changing this value can be found in C:\Program Files\JMP\JMP Live\JMPLive\.env.example.
|
|
–
|
If you anticipate that most of your traffic will be reading and commenting on posts, you might want to increase JMP Live's slice of the budget.
|
|
•
|
The value of DB_MAX_CONN_JMP_POOL in C:\Program Files\JMP\JMP Live\JMPPool\.env.
|
|
–
|
This value represents the maximum number of concurrent database connections that a single instance of JMP Pool attempts to sustain.
|
|
–
|
Basic tips for changing this value can be found in C:\Program Files\JMP\JMP Live\JMPPool\.env.example.
|
|
–
|
If you anticipate that most of your traffic will be republishing reports and interacting with reports (for example, using the Column Switcher or Local Data Filters), then you might want to increase JMP Pool's slice of the budget.
|
JMP Live Cluster
After installation, if JMP Live is started using the npm start command, then only one instance of the JMP Live server code starts. However, if JMP Live is started with the npm run cluster command, then multiple instances of the JMP Live server code start. Using cluster mode, if one instance is busy, a client can still get a response from another instance. The normal way of operating is to use cluster mode. The number of JMP Live server instances in a cluster is approximately equal to the number of cores present on the server.
Sample Budget
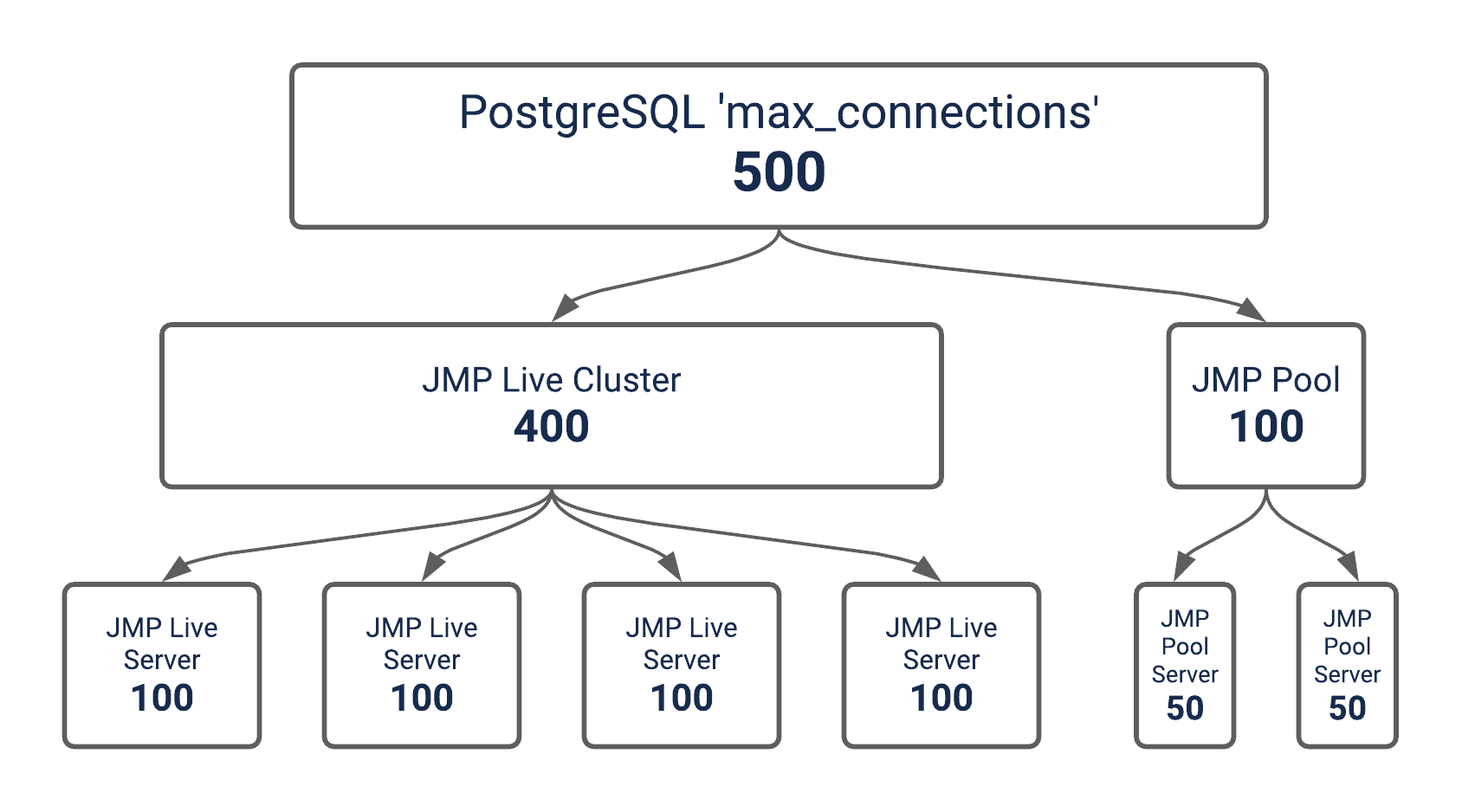
Here is a simple example showing a total budget of 500 connections, with 4 JMP Live servers in the JMP Live cluster, and 2 JMP Pools. In this example, DB_MAX_CONN_JMP_LIVE is set to 100, and DB_MAX_CONN_JMP_POOL is set to 50.
Figure 1.38 Example of Sample Budget
Technological Notice
The JMP Live software is provided with certain free and open-source software identified in the Help > Notices section of the customer’s JMP Live page, and also at the following link: https://support.sas.com/en/documentation/third-party-software-reference/licenses.html.